
Facebook Scam
Facebook Scam: Stay Informed and Protected from Social Media Scams
Facebook scams are becoming more sophisticated, targeting unsuspecting users to steal personal information and money. Stay informed and protected with our expert guidance on recognizing and avoiding these scams. By following our tips and insights, you can navigate the digital world with confidence and safeguard your online presence.
**Recognize Common Facebook Scams**
Understanding the types of scams on Facebook is crucial. Scammers often use phishing links, fake profiles, and deceptive ads to trick users. Learn more about [common Facebook scams](https://www.facebook.com/help/167471764612320) and how to identify and avoid them.
**Protect Your Personal Information**
Safeguarding your personal information is vital for online security. Avoid sharing sensitive details on social media, use strong passwords, and enable two-factor authentication. Get comprehensive tips on [protecting your personal information online](https://staysafeonline.org/stay-safe-online/protect-your-personal-information/).
**Stay Updated on Cybersecurity Trends**
Online threats are constantly evolving. Stay informed about the latest trends in cybersecurity to understand the risks and how to mitigate them. Follow the [latest trends in cybersecurity](https://www.cybersecurity-insiders.com/) to keep your knowledge current.
**Fortify Your Online Defenses**
Proactively securing your online presence is essential. Regularly update software, use antivirus programs, and be cautious of suspicious links and messages. Explore ways to [fortify your defenses against online threats](https://us-cert.cisa.gov/ncas/tips).
**Follow a Comprehensive Guide to Internet Safety**
For a broader understanding of how to stay safe online, consult resources that cover various aspects of internet security. Our [comprehensive guide to internet safety](https://www.consumer.ftc.gov/topics/online-security) offers valuable information to help you navigate the web securely.
Arm yourself with knowledge and become a savvy defender of your online presence. Let us be your trusted ally in the ever-changing landscape of internet safety. By staying informed and proactive, you can outsmart scammers and effectively protect your personal information.

Best Fix for Windows 10 crashing photo app in 5 second
Best Fix for Windows 10 crashing photo app in 5 second?
Best Fix for Windows 10 crashing photo app in 5 second. Not able to do anything. I tried many things such as download Microsoft fix it tools, did not work, run troubleshooter from control panel, did not work. Then tried shell:libraries command to re-create folder, did not work. App restore did not work…and so on. Finally, one thing work and I would like to share with you guys. Remove photos app and re-install it again. But you have to Remove phots app using PowerShell. Here is the Steps: Click on search and type PowerShell then you will see Windows PowerShell (not case sensitive) Take mouse over it and right click on it and click on Run as Administrator. The type this command: Get-appxpackage *Microsoft.Windows.Photos* | remove-appxpackage This command will remove the photos app Now go to start and type store it will bring Store (Trusted Windows Store App) click on Store and then type on search box Photos its free Click on free and install After completing installation open your picture. And enjoy!! If it works for you share it to help someone else. Enjoy! Thank you! Beware of Microsoft Scam
Vlog
Vlog-YouTube

Beware of Microsoft Phone Scam
Beware of Microsoft phone scam
Hi my friends be careful who you give remote access to your computer. Even if they say they are calling from Microsoft, first Microsoft will never call, even one’s computer is very badly infected. Once you purchase a computer it is your responsibility to protect it from viruses, malware, hackers and so called Microsoft tech s(they are not from Microsoft) they are from MICROTOSH SOFTWARES sound like Microsoft and MICROTOSH computer support number is 855-601-0002, block this number. Beware of Microsoft phone scam.
One of my yearly clients gave them access to her computer. They locked her out of her own computer, charged her $499 and asked for more before she hung up and called me in a short time, they had already had modified her registry file. So she couldn’t do anything but call their number and let them control her pc.
I went to fix her computer and she did not pay a dime to me nor the hackers. I helped her cancel her credit card and did whatever it took to dispute her amount.
She bought a LPC (Lexington PC Clinic) yearly plan and LPC (Lexington PC Clinic) fixed everything. Her computer is now running like it was before. Beware of Microsoft phone scam.
Don’t get scammed. Call us.
I did some research here is the result:
Googled MWS
MICROTOSH SOFTWARES AKA MWS PC Security
Gov Consumer information
Fake Security Scams – 2015 Edition from Webroot
Alert: Computer Repair Scam Using BBB Name
Avoid tech support phone scams From Microsoft official
PC Advisor
 |
 |
 |
|---|
hack a Chromebook
Google will pay $100K if anyone can hack a Chromebook
Hack a Chromebook, Get Rich or Hack Tryin’
Since 2010, google paid to researchers over $2,000,000 to find security vulnerabilities in Chromebook hardware and software through Google’s Security Reward Program to make google user safer. Google takes Its chrome security very seriously. Google made some changes in “hack a Chromebook” bounty reward program from $50,000 to $1000,000.
Google has offer $50,000 last year for hack a Chromebook in guest mode. There was no successful submission. So, google increase its reward to $100,000, available all year around. Not only for Chromebook, google has been paying for wide range small security vulnerabilities test.
Reward range from $500 to $1000,000.
Happy Hacking
Official Links:
 Application Security
Application Security
The Chromium Projects
Sources:
Google: We’ll pay $100k if you can hack a Chromebook remotely
Google says hack Chromebook, get $100K richer
Google Will Pay You $100K If You Can Hack a Chromebook
After 0 successful submissions, Google doubles top reward for hacking a Chromebook to $100,000.
Google will pay you $100,000 if you can hack a Chromebook
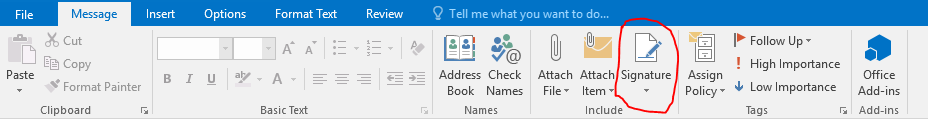
Add a signature
Add a signature automatically to every outgoing message in Outlook 2016
Do you get annoyed when you do not see your signature in HTML format when you reply message? Here how you set it up to
Add a signature automatically
when you click on reply or forward. It will appear as it shows up for new message.
Click on New Email
Click On Signature and drop down list will appear with your signatures
Select Signature.. you will see your name too but just click on Signatures.
Then click on drop down on Replies/Forwards: and select your name or Signature however you have save your signature.
Then click on ok
How to update Drivers on your Windows Computer..
There is No Shortcut to Safeway to update Drivers on your Windows Computer..
How to update Drivers on your Windows Computer? Looking for drivers to update your computer hardware? Avoid using any kind of Driver-Update softwares and I would recommend that avoid download any driver update or finder software from freeware-download sites. There are many driver update software’s advertisements are on the net, just beware of what you downloading. Those are the software will cause you some problem in long run.



The best way to update your hardware driver to go to device manufacture website to download drivers because they keep updating their driver version. HP, Dell, NVIDIA, AMD’s Catalyst Control Center, Realtek, or whichever is in your computer. These all have auto scan hardware in their website. They will find right version for your hardware. Usually graphic card often appears in your system tray.
Or let windows update to do the work. Windows has its own inbuilt update driver software. Windows 7, 8 and 8.1 will update your driver through windows update but now with new Operating System, Windows 10 Microsoft being more progressive and forceful, so Windows 10, Windows update will automatically download and install the latest driver. Even if you add any hardware it will overwrite and install latest driver for you.
So stick with windows update or manufacture website.
Here is some more to read: Malware Tip
Internet Explorer Security Alert “Secure Connection”
When you are browsing the internet using the IE browser and each time you go to the next page and you get a pop-up message “you are about to view pages over a secure connection or about to leave the secure connection” you have to click “Yes” before you go to next page. It is very annoying frustrating to click every time. So, I have step by step directions on how to fix this. Also, make sure your Windows updates are up to date. Because windows updates are very important for your computer security.
Is your internet explorer prompt you with this message “you are about to view pages over a secure connection or about to leave the secure connection” And It annoying.
If you want to get rid of the Security Alerts that you are about to view pages over a secure connection or about to leave the secure connection? prompt, here is the steps:
Open Internet Explorer or Lunch IE
Click on In Gear Icon and select Internet Options. Picture below
Click on Security Tab
Click on Custom Level
Scroll down and you will find Miscellaneous section
Under miscellaneous you are looking for Display mixed content click on Enable
Click on OK. Close IE (Internet Explorer)
How to fix Temporary profile in windows 7, 8, 8.1 and 10
 Restart your computer.
Once you see boot screen, start taping on F8 on your keyboard. You will see this screen:
Now use down arrow on keyboard to select Safe Mode
And hit Enter
For Windows 8, 8.1 or 10 go to settings startup and safe mode
It will log you in safe mode with administrator account credential.
Now save all your data before you fix temp user profile error. I suggest you save your data.
Now, the location of User ProfileList is here:
HKLMSOFTWAREMicrosoftWindows NT CurrentVersionProfileList
Restart your computer.
Once you see boot screen, start taping on F8 on your keyboard. You will see this screen:
Now use down arrow on keyboard to select Safe Mode
And hit Enter
For Windows 8, 8.1 or 10 go to settings startup and safe mode
It will log you in safe mode with administrator account credential.
Now save all your data before you fix temp user profile error. I suggest you save your data.
Now, the location of User ProfileList is here:
HKLMSOFTWAREMicrosoftWindows NT CurrentVersionProfileList
 Make a registry backup- It is very much recommended-Right click on profile list and click on export-choose the location to save this file.
Now find the corrupt profile, rename it with .bak extension. If you don’t know how to make .bak extension follow these step first:
Navigate to HKLMSOFTWAREMicrosoftWindows NTCurrentVersionProfileList
There should be a multitude of Registry keys inside the ProfileList, Look for two identical ones which are differentiated by the .bak extension (e.g. S-1-5-21-XXXXXX1234.bak & S-1-5-21-XXXXXX1234).
The Registry key with the .bak extension contains the user’s actual profile while the one without the .bak contains the Temp profile.
Delete the Registry Key WITHOUT the .bak extension and rename the one with it to S-1-5-21-XXXXXX1234 (without the .bak). Notice the fields on the right, there should be a value named RefCount, change the value to 0.
Reboot the machine.
And this will fix your temp user profile problem.
Make a registry backup- It is very much recommended-Right click on profile list and click on export-choose the location to save this file.
Now find the corrupt profile, rename it with .bak extension. If you don’t know how to make .bak extension follow these step first:
Navigate to HKLMSOFTWAREMicrosoftWindows NTCurrentVersionProfileList
There should be a multitude of Registry keys inside the ProfileList, Look for two identical ones which are differentiated by the .bak extension (e.g. S-1-5-21-XXXXXX1234.bak & S-1-5-21-XXXXXX1234).
The Registry key with the .bak extension contains the user’s actual profile while the one without the .bak contains the Temp profile.
Delete the Registry Key WITHOUT the .bak extension and rename the one with it to S-1-5-21-XXXXXX1234 (without the .bak). Notice the fields on the right, there should be a value named RefCount, change the value to 0.
Reboot the machine.
And this will fix your temp user profile problem.
Mac is not immune to malware
Mac is not immune to malware
Protect your Mac from Malware
Protect your Mac from Malware. Mac is not immune to malware or virus anymore. People have a common belief that Macs are safer than PCs. It is a common belief that all the viruses are designed to infect Windows computers, not Mac. There are many websites where one can find detailed information about windows malware, but one has to do a lot of research to find out information about Malware for Macs. Here is the list of Trojan malware since the 1990s.
This article not to make you panic or frightened this is just to make you aware of the common belief that Macs are immune to Malware. Today, I was reading an article on Macworld, and I end up landing an exciting page about Malware on Macs “List of Mac viruses, malware, and security flaws” to support my article. Protect your Mac from Malware.
There is no computer system is immune to malware (Malicious Software), even Mac / Apple Systems.
MacDefender and Flashback are the most vulnerable.
Flashback: Flashback virus target security hole in Java. Java is included in OS X (OS X is Operating System such as Snow Leopard, Lion, Mountain Lion, Mavericks, and Yosemite). Flashback virus is designed to steal your data or information in the background without even the user noticing. Once your computer is infected you might not see any difference the way your Mac runs.
MacDefender: Also known as Mac Protector, Mac Security, Mac Guard, Mac Shield, and FakeMacDef is Internet rogue security software that will mislead the user into paying money for fake or simulated removal of malware a form of ransomware claim to remove malware from the computer, instead of removing it introduce malware to the computer.
Recently one of our mac was acting funny; slow process, popups and not shutting down properly. I find out that there were popups and adware, here is a picture that you can see.
So yes Mac does get infected. So Protect your Mac from Malware.
Protect yourself by doing this step:
Make sure your Mac Malware database is always up-to-date if you want peace of mind, take an action: Go to System Preferences
- Open App Store Preference
- Check – Automatically check for updates.
- Check – Download newly available updates in the background. (You will be notified when the updates are ready to be installed.)
- Check – Install app updates
- Check – Install OS X updates
- Check – Install system data files and security updates.
Last one up to you:
- Check/ uncheck – Automatically download apps purchased on other Macs.
This will keep your Mac free from the most malicious software. Also, it is very unlikely, it doesn’t help you to install malicious software on your Mac. If you want to strict installation do this:
- Go to System Preferences
- Open Security and Privacy
- Allow apps to download from:
- Check – Mac App Store and Identified Developers.
This will strict the installation process. Check out Lexington PC Clinic YouTube channel, we have a YouTube video step by step direction to Protect your Mac from Malware.
Also, get antivirus for mac.
See you again with a new topic. LPC
If you need computer repair, virus removal, malware removal, Laptop screen replacement, iPad, iPhone, Samsung Galaxy Screen Replacement, Mac repair. Contact Lexington PC Clinic. Or Call at 859-408-0948.
Dear Readers and Viewers of Lexington PC Clinic,
The computer is my passion and it is my profession too. I troubleshoot and computer repair every day. I write a blog and do YouTube videos on weekends in my workshop. This
Computer Repair blog is for me to educate everyone on current computer issues that I come across while troubleshooting, such as repair Samsung Galaxy screen, repair MacBook Pro, MacBook Air, iPhone, Galaxy, Windows laptops, Virtual box, replacing hard drives, adding memory, disassembling/teardown of smart phones, laptops, iPads, Surface computer and phone scam.
I blog about and post YouTube videos so you can troubleshoot simple computer problems for yourselves.*
Check out my YouTube channel at: https://www.youtube.com/c/Lexingtonpcclinic for my viewers.
No problem is too small or too big. Ask me via email at lpc@lexingtonpcclinic.com leave a comment on my page. Or ask me on my Facebook page: http://www.facebook.com/LPC247.
I try to answer all questions on the weekends. Like and subscribe to my YouTube channel and Facebook page for updated contents.
Thank you
Keep reading and keep watching videos.
Lexington Pc Clinic
NOTE:
*Self-diagnosis of computer problems or following videos and/or general advice is at your own risk. Lexington Pc Clinic is not responsible for any damage or data loss.















Recent Comments